The 5 Best Communication Protocols of 2026!

In this digital era, communication is rapidly increasing, getting faster and convenient for people across the globe. From sending messages over letters to today’s digital direct messaging, communication has evolved to fit right within our palms. But how do we know these systems are reliable and safe to use? This is where Communication Protocols steps in.
In this article ahead, we will discuss about,
- What communication protocols are all about.
- Their pros and cons.
- And finally, discover which one will best suit your needs.
So, let’s jump-start right away!
Table of Contents
What are Communication Protocols?
A communications protocol is a set of instructions on how to send or share data between devices that are connected over a network. These rules cover how the data in an app should be structured, what it means, when to send it and how to fix issues when they occur.
Why are Communication Protocols Important For Your Business Apps?
Do you own a business app or are interested in developing one with interaction features? Then you might want to consider getting to know the basics of communication protocols. These protocols define how the information exchange happens between user devices via your app. You’ll need to ensure that these protocols are set up right to stay confident about the security and smooth technical functionalities.
5 Most Popular Communication Protocols in 2026
1. HTTP/1
Hypertext Transfer Protocol, or HTTP / 1.1, is an application protocol that exchanges data between user devices and your app server. This protocol was developed by Timothy Berners-Lee in 1989.
How Does It Work?
When you set up this protocol, the data exchange between user device and your server happens as follows:
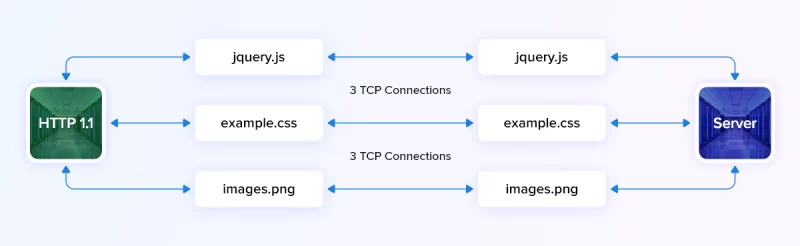
- Step 1: The user device (client) sends a text based request to your server.
- Step 2: When the server receives this request, it will start loading the response as a set of resources.
- Step 3: The response one after another and traverse to the client device.
- Step 4: The response reached the client in the form of an HTML page.
Note: The resources cannot be loaded all at once. Which means, if one of these resources cannot be loaded, it will block all other resources lined up behind.
Interestingly, this data exchange happens in two way with HTTP 1.1:
i. Short Polling
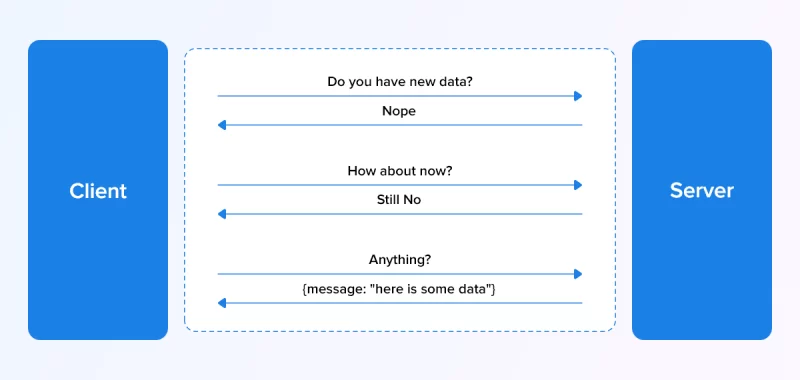
- During short polling, the user device (client) sends multiple requests until your server responds with new data.
- After receiving this response, it starts with new requests to get the next new data. This process keeps repeating continuously.
- This type of polling is considered as an ineffective data transfer method as a lot of resources and time is wasted during the parsing of requests and responses.
ii. Long Polling
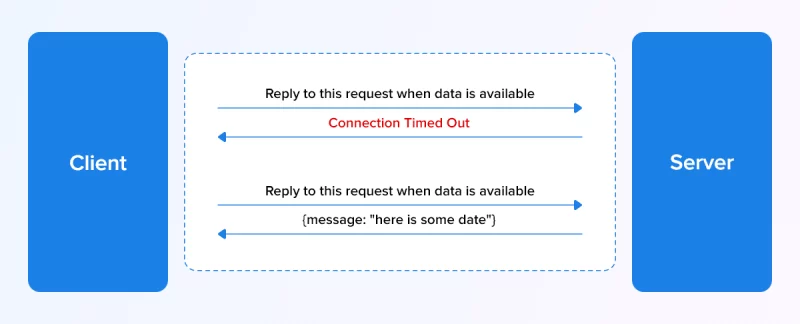
- In long polling, when a client device makes a request, your server will keep the connection with the device open.
- It does not terminate the connection until new data is available.
- After the client receives this response, it initiates a new request, and the server opens a new connection to handle this new request.
Thus, considering real-time connection for apps- neither short polling nor long polling sound efficient for effective real-time connection requirements. So it’s time to look into its successor – HTTP/2
2. HTTP/2
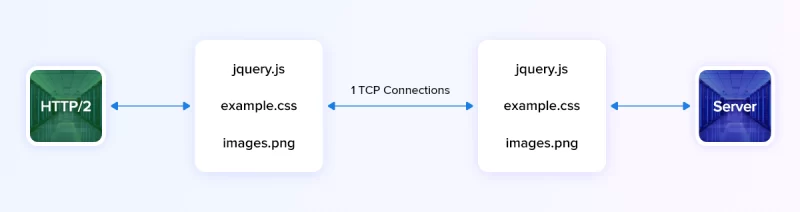
HTTP/2 is more or less an enhanced version of the HTTP protocol. It discards all the limitations in HTTP, without any change in the semantics. Since this protocol allows only one persistent connection for multiple requests, it is considered more effective in utilizing the resources resulting in improved performance and speed.
How Does It Work?
HTTP/ 2 uses the framing mechanism to exchange data between the client and server.
💡 Quick Note:
What is a Frame? A frame carries unique data sets containing the metadata needed for the communication exchange. These frames combined together form a message. This message is the request or response of the process. A series of messages are combined and transferred as a stream.
Unlike HTTP/1, this protocol uses only 1 connection for the entire data exchange process and handles the request and response in two ways:
1. HTTP/2 Multiple Stream
- Step 1: When a request is initiated, a TCP connection opens
- Step 2: The data starts following as a stream without getting blocked at any point
- Step 3: The TCP connection closes only when the request is completely fulfilled
2. HTTP/2 Multiplexing Stream
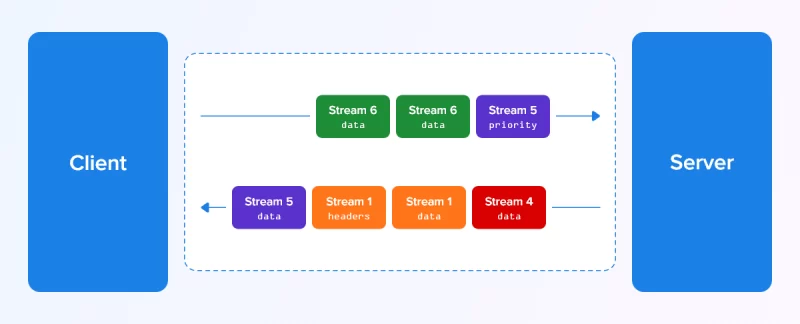
- Step 1: The client and server breaks down the HTTP message into individual frames at the binary framing layer.
- Step 2: These frames are interleaved and reassembled
- Step 3: Finally, these reassembled message reaches its respective endpoints
3. WebSockets
Websockets are full-duplex, bi-directional protocols that establish connection between client and server via a single open connection. With websockets, connection happens bi-directionally, making data transfer capable for real-time communications.
How does it work?
In a Websocket connection, a normal HTTP/1.1 protocol is used to make the first handshake between the client and the server. This handshake bridges the HTTP and Websocket protocols.
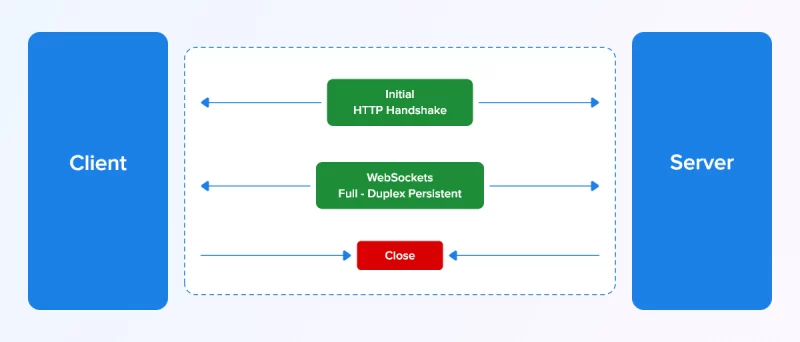
Here is how this connection is established:
The Request:
Connection: Upgrade Header represents the Websocket Handshake
Sec-WebSocket-Key represents a random value with Base64-encoded. For every handshake, this value is generated. Apart from these, the request also contains a key header
When these headers are combine, the HTTP GET request look something like this:
GET ws://websocketexample.com:8181/ HTTP/1.1
Host: localhost:8181
Connection: Upgrade
Pragma: no-cache
Cache-Control: no-cache
Upgrade: websocket
Sec-WebSocket-Version: 13
Sec-WebSocket-Key: b6gjhT32u488lpuRwKaOWs==The Response:
Sec-WebSocket-Accept is the response header that represents the submitted value in Sec-WebSocket-Key request. These headers are connected with unique protocols in order to avoid API security risks.
On a successful request, the response will look similar to the below sequence:
HTTP/1.1 101 Switching Protocol
sUpgrade: websocket
Connection: Upgrade
Sec-WebSocket-Accept: rG8wsswmHTJ85lJgAE3M5RTmcCE=4. gRPC
gRPC (Remote Procedure Call) is an open-source framework initially developed by Google. It simplifies complex networking infrastructures by connecting services with pluggable supports.
Above all, gRPC can create cross-platform binding between clients and servers. It allows client apps to directly call methods that run on a server app installed in a different machine.
How Does It Work?
gRPC creates a protocol buffer compiler right from service definition to generate client- and server-side code. The protocol is used to call the APIs on the client side. In retrospect, the implementation of the APIs take place on the server side.
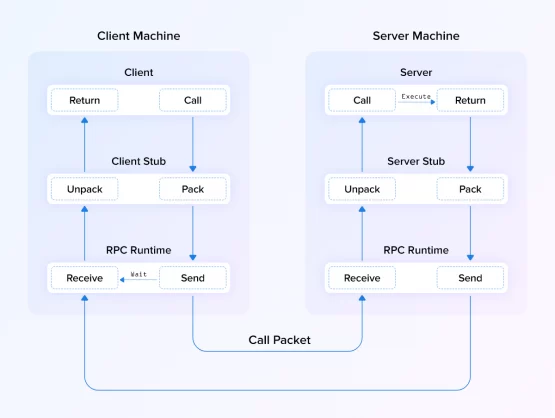
Server Side:
- Step 1: The Service declares the methods
- Step 2: The server implements these methods and handles the client calls using gRPC
- Step 3: gRPCs decodes the incoming requests
- Step 4: Runs the service methods
- Step 5: Encode the service responses
Client Side:
- Step 1: Similar to the service on the server side, the client side uses stub, a local object to declare the methods.
- Step 2: The client implements these methods and handles the calls with the right protocol buffer message type
- Step 3: Meanwhile, gRPC takes care of the server requests and the buffer responses of the server protocol.
5. WebRTCs
WebRTC is an open source protocol that supports exchange of text, voice, video, or any generic data between user devices in real-time. The foremost advantage of using Websockets is that it is an open standard that does not require a server to establish communication between peers. Consequently, it immensely reduces the latency when any form of communication takes place.
How does it work?
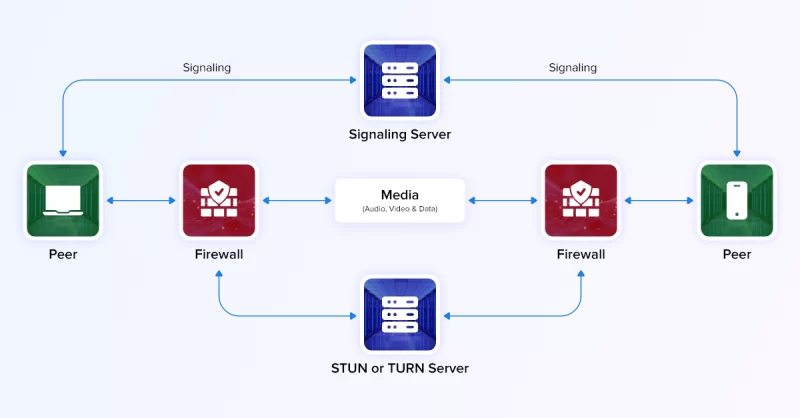
Step 1: Signaling
This process sets up and controls the entire communication session. Signaling is where the real-time data is sent to the server for encoding and then delivered to the peer.
Step: 2 Connection
Next, two or more peer devices need to be connected. This step involved ICE servers, which generate unique agents for each candidate (transport address). Using these candidates, the STUN and TURN servers connect the peers, wherever they are located.
Step 3: Security Implementation
WebRTCs use Datagram Transport Layer Security (DTLS) and Secure Real-time Transport Protocol (SRTP) to encrypt and secure user data.
Step 4: Communication
When you implement WebRTCs, you will have to establish unlimited data transfer between user devices. Be it voice, video or large media files, the communication needs to be right on time. Hence, WebRTCs use the Real-time Transport Protocol (RTC) and Real-time Control Protocol (RTCP) protocol for live data transfer.
When Should You Use These Protocols?
The use case of these protocols largely differ from each other. However, you may need to choose the protocol that rightly fits your requirement. So, here is a quick checklist for your reference:
HTTP
- To establish bidirectional communication
- When you need to use gRPC or WebSockets
WebSockets
- For real-time applications
- Small amount of data transfer
gRPC
- Suited for large data transfer and small API calls
- When implementing microservices with different programming languages
WebRTC
- Real-time communication
- Low latency
- Large data transfer
- Direct use on browser
Conclusion
Made the right pick? We hope this article has done a fair job in helping you analyze the best communication protocol for your apps. Several other protocols are on the rise and stay in touch with us to get interesting updates on them.
And we don’t stop here. As a team of tech enthusiasts, we’d love to cover more about the topics you wish to delve into. Post in a comment and we’ll take care of the research. Until then, happy development!
Get Started with MirrorFly’s Secure Chat Features Today!
Drive 1+ billions of conversations on your apps with highly secure 250+ real-time Communication Features.
Request Demo200+ Happy Clients
Topic-based Chat
Multi-tenancy Support

Frequently Asked Questions (FAQ)
IoT, or Internet of Things, is a concept that refers to the interconnection of physical devices through the Internet. IoT enables these devices to communicate, share information, and be controlled remotely, often leading to automation and enhanced efficiency in various applications, such as smart homes, industrial processes, healthcare, and more.
There are several types of communication protocols that serve various purposes. Some of the popular protocols include:
- HTTP/1
- HTTP/2
- WebSockets
- gRPC
- WebRTCs
A network communication protocol is a standardized set of rules that govern how data is structured, transmitted, and received among different devices within a network. These protocols ensure that devices can effectively communicate and understand one another within the network by defining the specific procedures, data structures, and restrictions that must be followed.
VoIP (Voice over Internet Protocol) uses special protocols to work. One of them is RTP, which handles audio and video. To set up calls, it also uses signaling protocols like SIP and H.323. These protocols help VoIP phones talk to each other over the internet.
A data communication protocol is a set of rules and conventions that govern how data is formatted, transmitted, and received in a data communication network. These rules ensure that devices or systems can communicate with one another effectively by defining the structure, timing, and error-checking procedures for data exchange.
Further Reading
Krishi,it’s a great…help me out to know more about communication protocols. Best wishes from the Indonesia
Very useful information and it is well arranged, so was pretty easy for me to read it. You’ve helped me to choose the top secure communication protocols. Thanks for the article. Great work!
The Best list. I am doing some research for the secure communication protocol. This list helped a lot to learn additional info. Thanks for the article.
Amazing Blog! Thank You.. the article is really helpful. It taught me the best protocols for communication. Thank You for sharing your insights.
Thanks. I found a few good ideas in your article and choosing best communication protocols for my business.
Hi, what aa super comprehensive list about best secure communication protocols. Thank your for taking the time to write it…. you have helped me a lot… I had never heard of them before I read your article.