What is Advanced Encryption Standard (AES) Encryption?

These days, it has become quite common for businesses and enterprises to focus on the encryption mechanism for their system as every log and every activity is going online. And the only savior to them turns out to be the AES-256 Encryption Algorithm.
Because, not only does it protect the system from third-party attacks, but it is also flawless, fast, and secure, and safeguards users’ online data and their daily transactions from prying eyes.
The best part is that even the government has accepted the AES Encryption Algorithm as the global standard in succeeding the former DES algorithm to protect any type of classified information. Such has AES and its types grown since its inception.
Therefore, in the blog post below, we will explore what is AES-256 Encryption, its types, its use cases, its working nomenclature, and why you should implement AES encryption in your system.
Table of Contents
What is an AES Encryption?
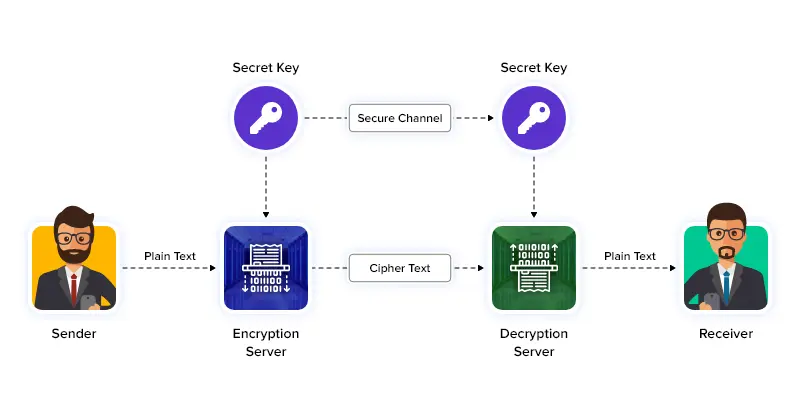
AES (Advanced Encryption Standard) is an even-block cipher encryption system that processes equal-sized blocks of data at a time to secure data and communications. It supports key sizes such as 128, 192, and 256. AES is widely used for computer security, data protection, and cybersecurity.
It is also known as the Rijndael algorithm or ‘block cipher’ that divides data into 128-bit chunks of sections called blocks.
Types and Highlights of AES Encryption
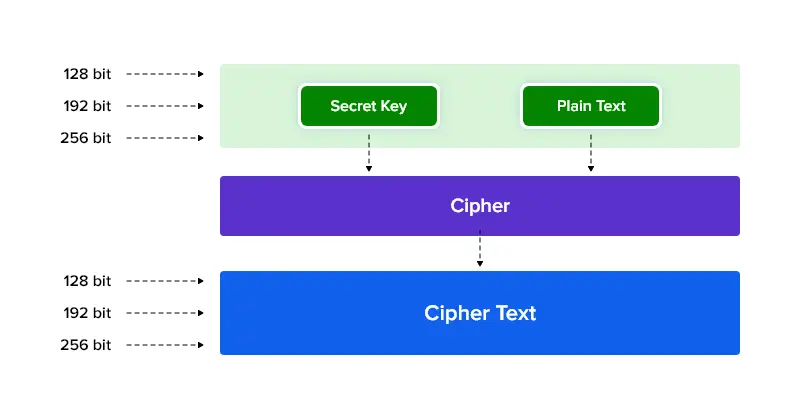
- AES encryption standard has three different key lengths of bit sizes 128, 192, and 256.
- The AES encryption key divides data into 4*4 arrays containing 16 bytes each.
- Each of these bytes contains a maximum of 8 bits and this division does not change the size of the cipher text.- Finally, the algorithm uses a substitution-permutation network (SPN) to encrypt data by applying multiple rounds to the plain text. For instance, AES-256 uses 14 rounds of encryption, making it more secure than its lower version, AES-128, which uses 10 rounds.
Here’s a concrete example of the AES algorithm in cryptography, meaning let us see what a ciphertext looks like:
Plaintext Message: The acting president was diagnosed with a terminal illness.
CiphertextMesage: bWhVOg5IxuiUw1TKrEjFD4CCw9r30KcSp8LU49JXX89i5+K/Z55QeNgPnEoDtK90bbUjpbQZ/yaQGOdXlbZS9/Ntd/mfxnK6GAhyKmtHUUk=
(Source Credit: The AES encryption example that illustrates the ciphering of plaintext holds its originality from Trenton systems blog)
Fact: Did you know that people say that upon using AES 256 encryption (AES-256), there is a stipulated increase in the safety and speed of the information?
With the basics acknowledged, the next section is understanding its work nomenclature.
How Does AES Work?
AES itself is a vast topic that is quite difficult to understand even for the experts in this field. But, we have briefed this topic in the simplest form possible.
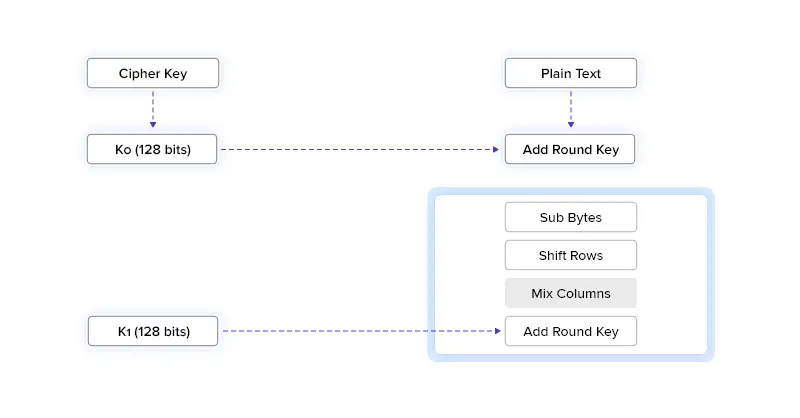
1. Block Division: We learned that AES is a block cipher that divides data into blocks of bits before encryption. This is the algorithm’s first step.
2. Key Expansion: In this step, AES creates new keys, preferably round keys for each round of encryption. It is done using Rijndaels’ key algorithm.
3. Addition Of Round Keys: Here, the initial round keys that were formed are added to subsequent data that has been divided.
4. Byte Substitution: Based on Rijndael’s S-box substitution method, every byte block is substituted with different bytes.
5. Row Shifting: The AES algorithm moves rows of divided data one space left to the second row, two spaces left to the third, and so on.
6. Mixing Of Columns: A new block of code is established by mixing or multiplying the columns of the divided data.
7. Addition Of Round Keys: Finally, round keys are added to the mixed columns.
Post this round, the process continues again 11 to 13 times depending on the key size of the AES encryption algorithm used.
What are the Features of the AES-256 Encryption Algorithm?
Below are quick details on the features that AES 256 algorithm renders, and the reason that makes it a globally standardized encryption algorithm.
- Encryption Rounds: As AES 256 uses 14 rounds to encrypt data, it is comparatively safe from hackers.
- Use of Bytes: The AES encryption software carries out its security operations on bytes and not bits, which means that it treats the 256-bit block size as 32 bytes.
- Network Structure: AES runs on SP network structure rather than the Feistel cipher, much similar to the DES algorithm.
Expansion of Keys: AES algorithm uses multiple rounds of encryption. In its first round, it uses a single key, which is expanded to multiple numbers in further rounds.
What are the Applications of the AES Algorithm?
The AES encryption algorithm also known as the Rijndael Algorithm works on an SP (substitution and permutation) format that encrypts its 128-bit blocks into cipher text. The algorithm uses keys of 128, 192, and 256 bits respectively to convert to an encrypted text.
It is because of this strong encryption type, the AES algorithm has now been widely used for diversified sectors. And, many businesses are now combining this technique with NIST – issued cryptographic algorithms to boost and enhance the encryption of business data.
Here’s a list of applications of AES that the algorithm stands tall:
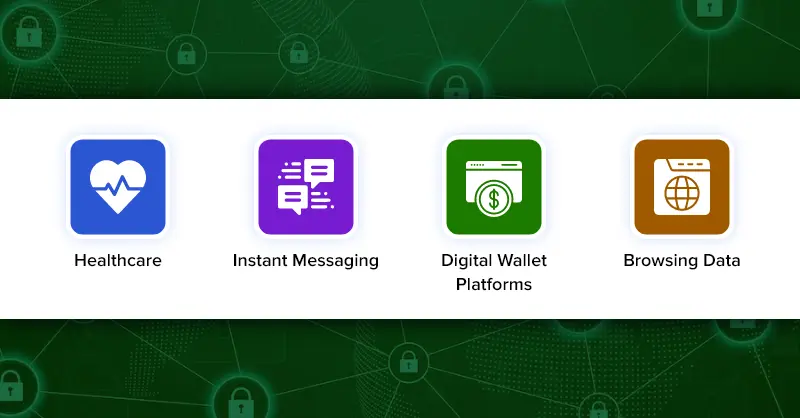
1. Healthcare – Patients’ data and all types of communication need to be secured and confidentiality must be maintained. For this, AES 256 – bit encryption along with a few other standards is approached.
2. Real-time chats or instant messaging – Businesses these days use session and public key types of the AES 256 algorithm to maintain the security of real-time chats. This algorithm has indeed kept personal conversations locked from all third-party intrusions. It also underpins Privileged Access Management systems, where AES encryption protects sensitive credentials and secure privileged sessions.
3. Digital wallet platforms – Name any type of payment platform, they are sure to have used AES for their encryption. However, what is the bit size to use depends on the transaction data. Some make use of 192-bit keys, whereas others use 256-bit for encryption.
4. Browsing Data: Your web browsers too may use AES to encrypt connections with any websites. It plays a huge role in providing authentication to the client and server-side computing.
We understand that it is a lot more to take in. But bet, without an insight on the below topic, your learning would be incomplete.
Why is It Important to Use AES-256 Encryption?
We are well aware of the happenings around us, and with everything going digital, we gave way for hackers to read our digital data. Therefore, keeping the privacy of data intact has become a vital role for businesses in the global field.
- And the best way they can achieve this is by opting for security solutions like AES 256 or other mechanisms. This ought to be on their bucket list always and at any time.
- Because only then will users have trust in us, strengthen their relationships with us, reduce liability for data, and finally could help us be devoid of hefty fines for data breach.
Hearing all these could be daunting, but can be very distraught for businesses who are into pre-made chat solutions like chat APIs and SDKs.
A small wormhole in the chat infrastructure can make pavements for cyber criminals to easily access users’ data. So, make sure to analyze the API providers then make a choice.
Choosing the best has to be done wisely.
MirrorFly’s AES 256 Encryption Doesn’t Mirror Inside Looks!
Well, we hope that we did a fair job in making you understand the true importance of AES encryption.
Now that you have an idea of the speed, versatility, and immunity that AES offers from cyber attacks, would you like to build your chat apps with AES encryption?
In such cases, look no further than MirrorFly, as our brainy in-house developers have taken care of the security and compliance part very well. With integral and robust chat libraries and extensions, developers can easily create real-time chat platforms that are secure and safe from any attacks.
Along with these, MirrorFly’s self-hosted chat SDKs comes with built-in security protocols just like our SaaS SDKs lets you conveniently host your apps on-premise
Ready To Build A 100% Secure Chat App Today!
Get 1000+ messaging features along with video and voice calling, into any web or mobile app with end-to-end encryption.
Request DemoComplete Ownership
Secure Infrastructure
On-Premise Hosting

Frequently Asked Questions (FAQs)
Yes, AES encryption is considered to be the most secure symmetric key encryption algorithm that is used to protect sensitive information from third-party intrusions. However, the security of an encryption system depends on the key size of AES used. The 256-bit variant of AES is virtually impenetrable because of the multiple rounds of encryption it undergoes and the complexity of the algorithm, whereas the 52-bit DES key can be cracked in less than a day.
AES-256 encryption is highly used by the federal government of the US to protect all types of classified information. Further, this type of algorithm can be used in a wide range of applications like:
- Online Banking or Financial Transactions
- Virtual Private Networks
- Promoting Database Security
- Personal and Official Communication
- Safeguarding Internal Devices
AES (Advanced Encryption Standard) encryption is a symmetric encryption algorithm that uses the same 128, 192, or 256-bit key for both encryption and decryption. Meaning, both the sender and receiver of a channel must share the same secret key for establishing communication.
Obviously yes, the AES encryption algorithm is considered to be an ideal option for securing all types of personal and official communications because of the different key size options available. The greater the key size used, which is 256-bit, 192-bit, and 128-bit, the more is time required to crack an encryption algorithm.
Yes! As AES-256 encryption uses a 256-bit key to convert plain text to cipher text, it is known to be the most strongest encryption algorithm for protecting sensitive information thus making it difficult to break by any computing force, brute force attacks, or common cryptographic attacks.
Related Articles
- How to Build A Flutter Video Call App in 2025?
- How to Build a React JS Video Chat App in 2025?
- How to Build an Android Voice and Video Calling App Using Java?
- Communication APIs: Top 7 In-app Chat, Voice & Video APIs
Wow what an Epic Blog post thank you so much and I am on the way to looking the types of aes-256 encryption. definetly this post will help me to get success
Thank you, Powlin for your kind words! I am really glad that you found my article to be informative and helpful for your journey toward understanding the concept of AES protocol. If you have any queries that need to be resolved or insights on this topic, please feel free to let us know.
This is really a great article. I just started looking for aes encryption algorithm details. this article realy helped me lot and time saver!!!
Thanks a ton, Vinay for your wonderful response toward my article. I’m glad and thrilled that you found my blog post to be helpful in your quest to understanding the concept of AES encryption. If you need any assistance on this topic, you may talk to our experts.
Never saw someone wrote this deep Guide on AES types and protocols used for aes algorithm . So deep it is, don’t have to look anywhere else. thanks keep writing
Really very glad that you found my article to be informative and helpful, Yugi! Thanks for such a wonderful response. We always strive to render in-depth information on any topic so that our readers gain fair insight on complex sections. My best wishes to you!
I think very very detailed article for those who try to know the AES encryption technology. Thanks for sharing!
Thanks, Rimna for taking the time to leave a wonderful response to my article. I’m really glad that you liked my blog post. If you have any doubts or want to see more content on topics related to this genre, let us know. Till then, best of luck!
Thanks for sharing. It is a very helpful content to know the full concept of AES Encryption as well as their apllications.Your blog is so amazing.
Thanks a lot Sachin for your kind response to my article. I am thrilled to hear that you found my post on AES encryption to be helpful. My best wishes to you.
I am genuinely glad to read this blog posts which contains lots of valuable data about advanced standard encryption and i also appreaciate that you are mentioned the clear data for how this encryption works and types, thanks for providing these data.
Hello Shameer, thanks a ton for your valuable and kind words on my blog post. Really glad that you found my article on AES and its types to be informative. My best wishes to you.
Amazing publish, very informative about aes-256 encryption. I’m wondering why the other specialists of this sector do not notice this. May I know Which protocol is used for AES?
Hello Rena, thanks for such a wonderful response to my article. I am extremely thrilled that you found my post on AES-256 encryption to be informative. To answer your query, AES being an encryption algorithm can be used with protocols like SSL/TLS to provide safe and secure E2E encryption. If you have any doubts, please talk to our support team.
Excellent web site you have got here.. The clarity on your submit is simply great about the concept Advanced Standard Encryption (AES). It’s difficult to find high quality writing like yours these days. I truly appreciate individuals like you!
I really appreciate your positive feedback on my article Smith! Glad that you liked my post and my writing style. Please keep visiting us for more insights on in-app chat-related features and others. Best wishes to you!
Excellent blog mate. Very detailed info and broader options are covered about AES encryption protocols. Great job. Keep writing such wonderful article, I am sure this going to helpful for developer community. You should continue your writing. I am sure, you’ve a huge readers’ base already!
Thanks a ton, Nikilesh for such a wonderful response to my article. I really appreciate your positive feedback on my post about AES encryption protocols. Sure, we will soon meet again with yet another content on a specific topic, till then happy learning and sharing! My best wishes to you!!
Krishi, it’s a great…help me out to know the types of aes encryption finally
Best wishes from the Indonesia
Thanks Emitson, for leaving such a wonderful response to my article. I am glad that you were able to find the types of AES encryption helpful. We will soon meet again with yet another content on a specific topic. Best wishes to you too!